In the era of AI,
“Vibe coding” has become shorthand for a modern development style:
AI-assisted code generation, rapid iteration, fewer hand-written lines, and a strong focus on shipping fast.
This shift is powerful—but it also changes the security equation:
- Code is generated faster than it can be manually reviewed
- Engineers may not fully understand every dependency or edge case
- APIs are created and modified continuously
- Traditional security gates slow things down—or get skipped entirely
The question teams keep asking is:
If developers are coding by vibe, is security testing now QA’s job?
What QA Should Own
- Ensuring security tests exist and run automatically
- Validating coverage of APIs, flows, and auth scenarios
- Blocking releases when critical vulnerabilities appear
Security must be shifted left and scaled by automation.
Security Testing as a QA Automation Primitive
Modern security testing should co-exist with Test automation suite and it should feel familiar to QA teams:
| QA Automation | Security Automation |
|---|---|
| Regression tests | Vulnerability regression |
| Test coverage | API OWASP TOP 10 Vulnerability Coverage |
| CI failures | Security gate failures |
| Test reports | Security Testing Reports |
What is Pynt?
Pynt is an automated API security testing platform built for modern engineering teams shipping fast—especially in environments driven by CI/CD, AI-assisted development, and “vibe coding.”
At its core, Pynt focuses on real, exploitable API vulnerabilities, not noisy static findings.
What Pynt does well:
- Automatically discovers your actual API attack surface
- Tests authentication & authorization logic (BOLA, BFLA, excessive access)
- Finds business-logic and data-exposure issues
- Turns vulnerabilities into repeatable, CI-friendly security tests
- Fits naturally into QA and Dev workflows, not just security teams
Think of Pynt as QA-style automation, applied to API security.
How Pynt Bundles Naturally with Postman
Postman is where teams:
- Design APIs
- Explore endpoints
- Validate functional behavior
Pynt complements this by answering:
“What happens when these APIs are abused, misused, or attacked?”
Quick Integration Flow: Postman → Pynt
Prepare the Collection
Here I have downloaded DVAPI for practice purposes
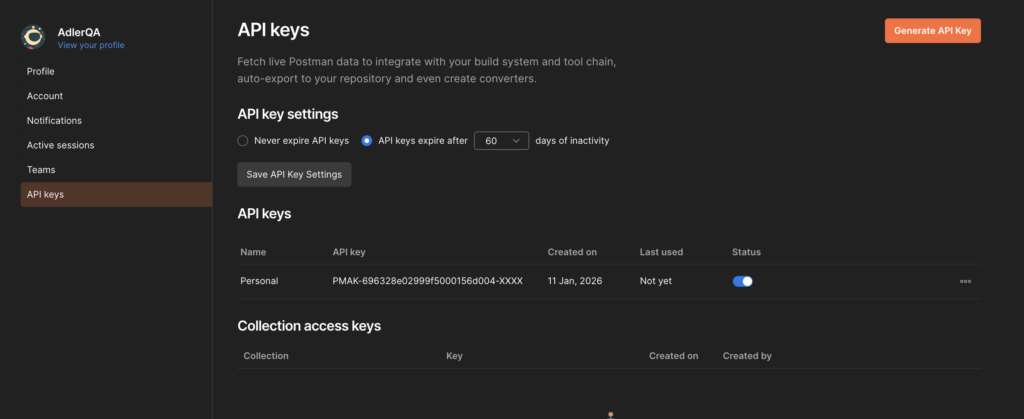
Generate Postman API Keys and copy the keys
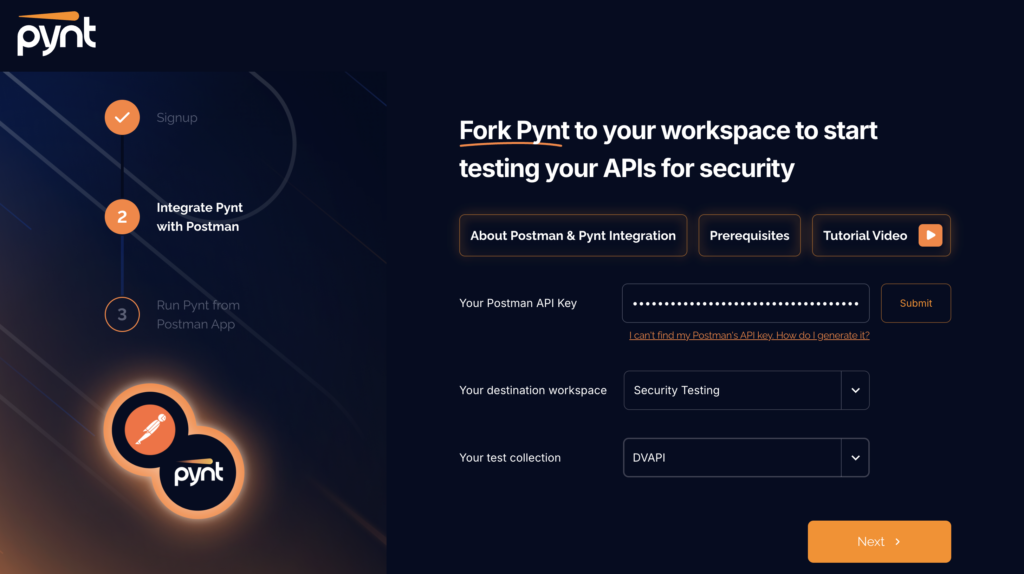
Navigate to Pynt
Signup to Pynt and Provide the generated API keys of Postman so that it can fetch all the collections
Choose the intended collection for which the security scans has to be performed.
Follow the installation procedures as per the guidelines provided by pynt. Python should be installed in the system as a pre-requisite.
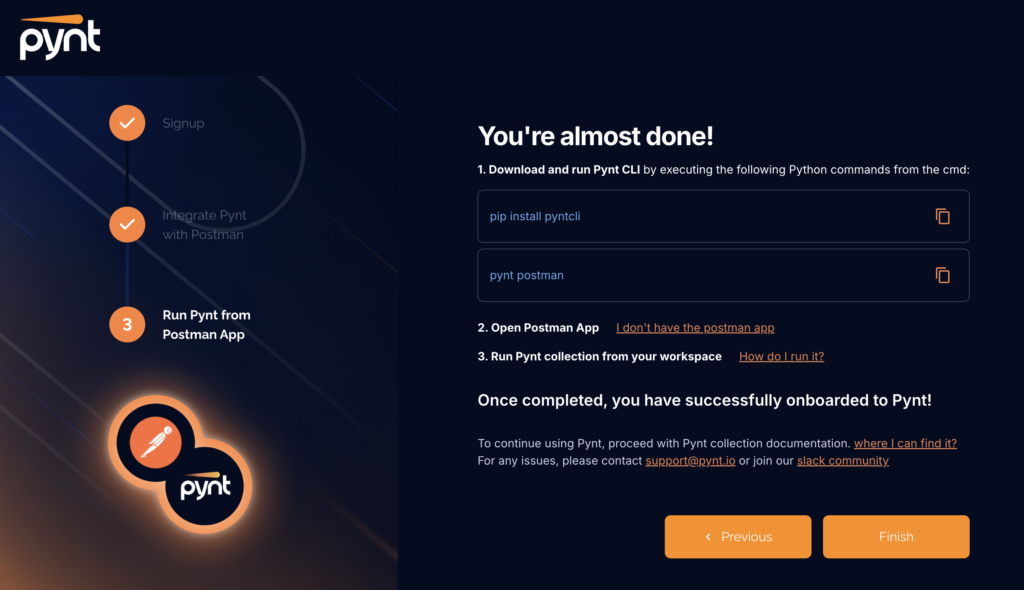
Once the setup is completed. Pynt gracefully integrates into the Postman collection.
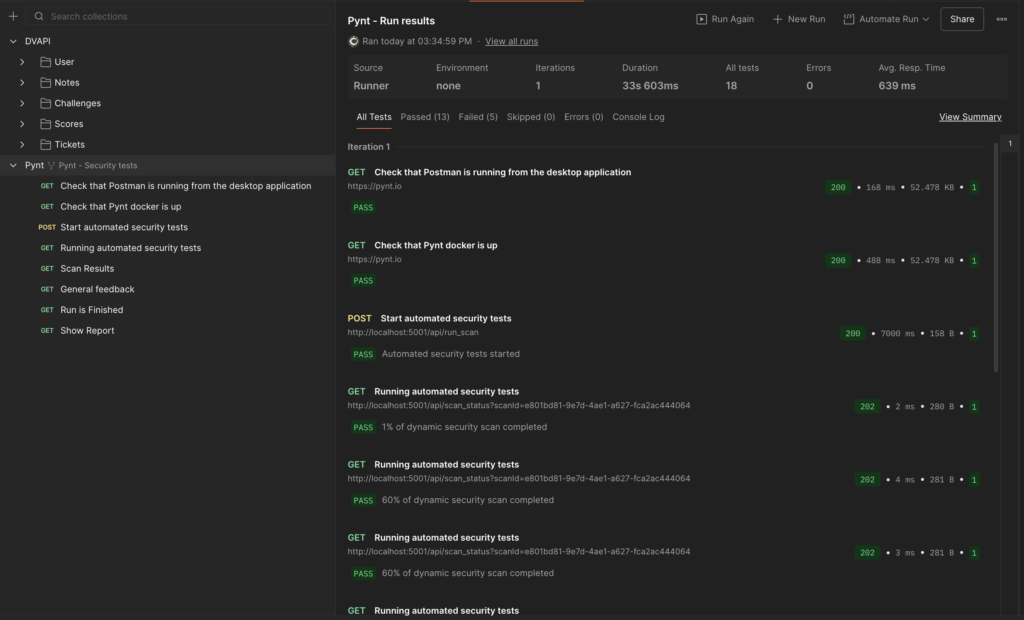
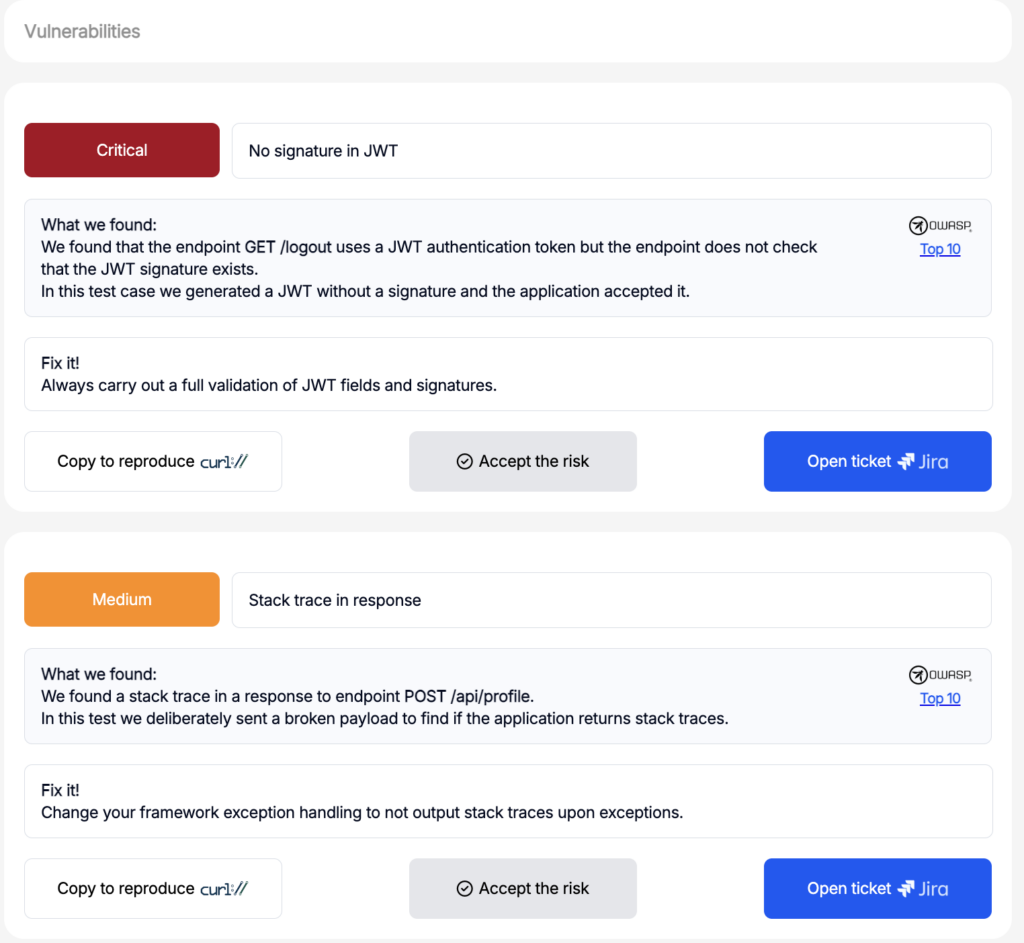
Execution and Result
Upon triggering the Pynt RUN from Posman, Pynt executes and provides detailed analytics
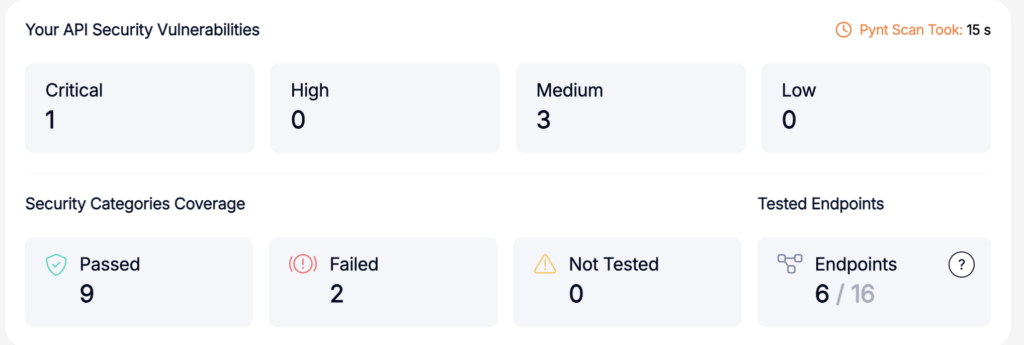
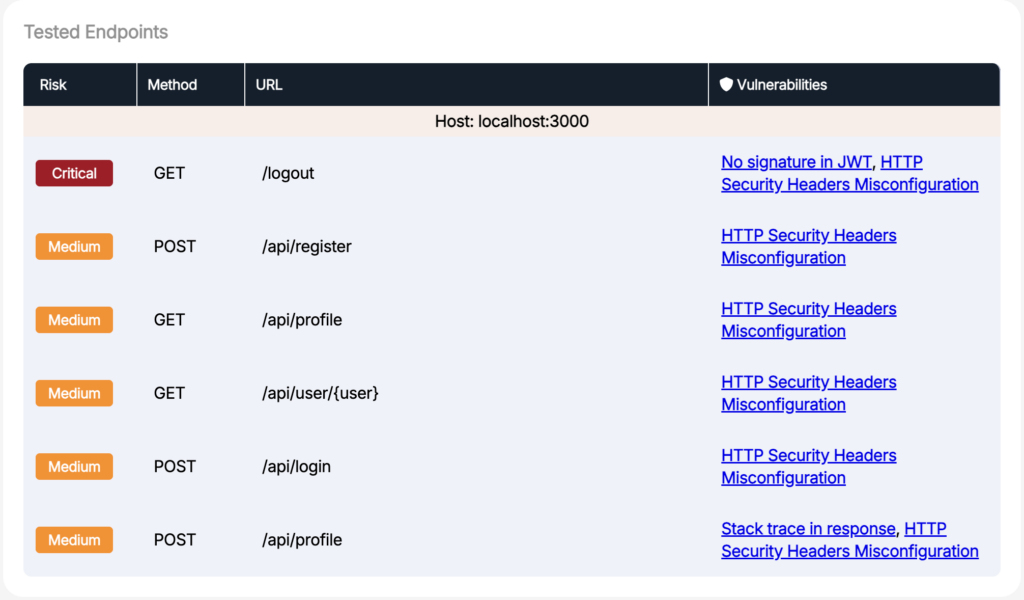
Quality and Security, Together
Security testing is no longer a standalone phase or the responsibility of a single security team. Instead, in today’s fast-moving, AI-assisted development environments, security testing is a fundamental part of software quality — and quality is where QA teams already lead.
When security testing is treated like QA automation — continuous, repeatable, and enforced through CI/CD pipelines — it scales naturally with development rather than slowing teams down. As a result, security becomes part of the delivery flow instead of a last-minute gate.
However, this does not mean QA owns security in isolation. Security is a shared responsibility across the teams. Meanwhile, QA ensures security testing is executed consistently and validated continuously before software reaches production.
Ultimately, in the era of vibe coding and rapid iteration, security that is not tested continuously is not secure. Therefore, without QA ownership of the security testing process, security efforts fail to scale and rarely last.